Your email is the gateway to the soul of your company. And hackers know it! In fact, according to a 2018 survey, 90% of cyber attacks and breaches started with a rogue email.
So, why do the bad guys specifically target email? They do it because IT companies have become so awesome! No… really! Technology protection has really improved over the years. Gateway protection has increased. Antivirus effectiveness has increased. So, now, the potential exploitable chink in a company’s armour is that 1 well-used route in… the route where a non-IT-trained human may be manning the door. All it takes is 1 click on 1 link.
Well, how do you spot a phishing email? To help you spot a potential attack, let’s look at a few examples.
The CRA are a popular agency that scammers love pretending to be, in an attempt to intimidate you into responding. They are relying on an emotional response. There are 3 red flags in this email.
The email address is definitely not from the CRA. Whilst they do sometimes email people, they will only ever send you a link to a page, form or publication that you ask for during a phone call or meeting with an agent. In fact, they have a great page on their website on how to avoid CRA fraud scams.
This email is not identifying who it was sent to specifically. (ie your name is not mentioned anywhere)
If you hover your cursor ( just hover… don’t click!) over the link, you will get a box pop-up showing you the actual web address if will take you to. Changes are it is NOT a legitimate site! (A quick google search from the real CRA website will verify that)
Not all scam emails are this simple, though. Some hackers are now getting better at making their email look legit. They will use logos to look more authentic or email addresses that are closer to the real thing.
It looks way slicker, but it contains the same red flags as the simpler CRA version:
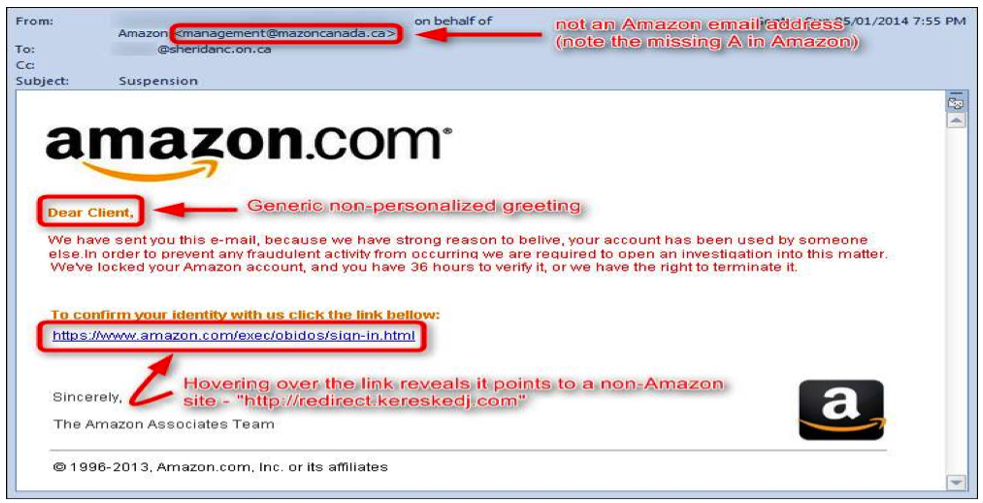
The email address is not an Amazon one… although, it does look VERY close. A quick glance may miss the fact that there is a letter missing from the word Amazon.
Again, a name is missing.
Hovering over the link reveals a non-Amazon website.
Here is another:
Once again, the email is using logos, the content looks genuine, correct spelling and grammar is used, and they have even made the link look like a genuine one. However, hovering over that link will reveal its true destination!
The Champion-Level Phishing Emails
More recently, we have seen a new level in phishing emails that look scarily genuine.
Here is an example, that appears to come from Microsoft themselves:
Scary, right? They have even spoofed an IBM email address. (Although, keen observers will spot that an Office 365 email will come from Microsoft rather than IBM!) Once again, your greatest defence is to hover over the links to see where they go. In this case, though, you would be much better off to just go to your Outlook account itself to see if there are any stuck emails in there.
Protect Yourself
Prevention (& protection) is definitely better than cure! This can be done with having the right configuration or your email, the best security tools (anti-virus, mailbox back-up etc) and educating all staff in the dangers.
So… to recap, here are the things to look out for to spot those dodgy emails:
Check the Sender Return Address – Does It Match the Company’s actual email? (e.g. something like Microsoft Security Team <MailTo: MichaelScott@OutlookMailMan.Com> looks close… but definitely not from Microsoft, whose email addresses end in Microsoft.com!)
Check the message content – How is the spelling & grammar? Does it create a sense of urgency? Wanting you to take action? Asking you click links?
Hover over URLS – Suspicious looking? (e.g. http://kjerjvitb.adomain.com/loadvirus/clickmypage.html )
Are you expecting it?
Don’t open attachments unless you absolutely know what it is. (Especially zip files! They are only needed for very large files like designs or presentations. A resume or similar word doc should not need to be zipped!)
Non-executable attachments (PDF etc) can redirect to a website
Have Backups! Backup your backups!
Don’t Login from any link! If you do want to check your account somewhere, open a separate browser and go to the official company's website login direct.
We hope that this helps your business avoid any future disasters. Ransomware from phishing links is an increasingly common and very expensive problem..
If you are still worried about being at risk, our team will be more than happy to help. We help many Fraser Valley businesses make sure they have rights safeguards in place. We are also experienced in coming to the rescue of businesses who have fallen victim.